ModSecurity uses can help block potential attack attempts from malicious users, but sometimes it can also block legitimate requests.
Note: Using SecRuleEngine Off in your modsecurity configuration, you won’t want to put that in your ModSecurity configuration file. As that completely turns off ModSecurity. The SecRuleRemoveById setting is used instead to only disable one specific rule.
If you are seeing errors in you apache log files for a domain such as:
[Sat Jul 25 16:34:57 2015] [error] [client ??.7.??.??] ModSecurity: Access denied with code 406 (phase 2). Pattern match "(?:\\\\b(?:(?:type\\\\b\\\\W*?\\\\b(?:text\\\\b\\\\W*?\\\\b(?:j(?:ava)?|ecma|vb)|application\\\\b\\\\W*?\\\\bx-(?:java|vb))script|c(?:opyparentfolder|reatetextrange)|get(?:special|parent)folder|iframe\\\\b.{0,100}?\\\\bsrc)\\\\b|on(?:(?:mo(?:use(?:o(?:ver|ut)|down|move|up)|ve)| ..." at REQUEST_FILENAME. [file "/usr/local/apache/conf/modsec2.user.conf"] [line "111"] [id "1234123404"] [msg "Cross-site Scripting (XSS) Attack"] [data ".cookie"][severity "CRITICAL"] [tag "WEB_ATTACK/XSS"] [hostname "domain.com"] [uri "/skin/frontend/base/default/js/cadence/lib/jquery.cookie.js"] [unique_id "VbQdIdg3u9IAAB9DPQkAAAAH"]
Mod _security is doing its job. If this is a valid script, you can make a change and allow it.
Run the following from ssh:
# grep ModSecurity /usr/local/apache/logs/error_log | sed -e 's#^.*\[id "\([0-9]*\).*hostname "\([a-z0-9\-\_\.]*\)"\].*uri "#\1 \2 #' | cut -d\" -f1 | sort -n | uniq -c | sort -n
The results will look like this:
# 100 1234123404 www.domain.com /skin/frontend/base/default/js/cadence/lib/jquery.cookie.js
ModSecurity rule ID 1234123404 has been triggered at least 100 times when accessing /skin/frontend/base/default/js/cadence/lib/jquery.cookie.js file.
In order to disable just the specific ModSecurity rule for the 1234123404 rule, run the following command:
# echo "SecRuleRemoveById 1234123404" >> /usr/local/apache/conf/userdata/std/2/userna5/domain.com/modsec.conf
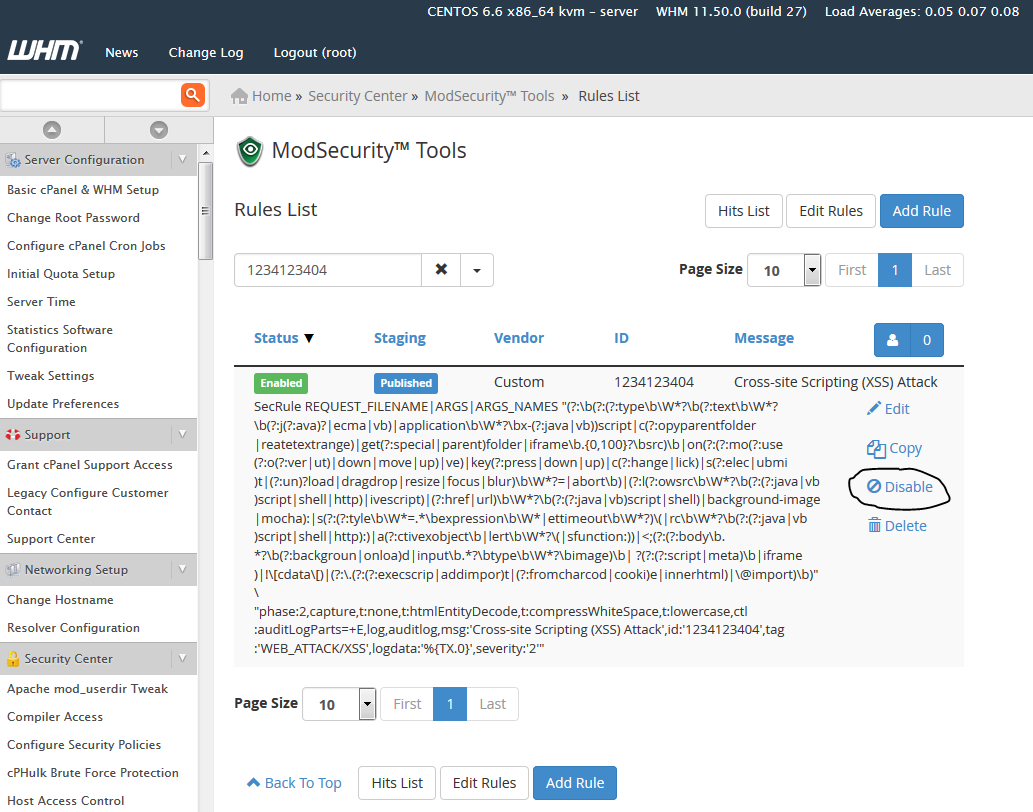
You can also search for the rule in WHM/cPanel at Home »Security Center »ModSecurity™ Tools » Rules List
Note the error in the log file – the ID:
# [id "1234123404"]
This is the rule. Search for this at Home »Security Center »ModSecurity™ Tools » Rules List.
You can click disable to allow the script.