The first step required for installing the agent is to configure the YUM repository. Modify the repository as follows:
echo -e "[r1soft]\nname=R1Soft Repository Server\nbaseurl=http://repo.r1soft.com/yum/stable/\$basearch/\nenabled=1\ngpgcheck=0" > /etc/yum.repos.d/r1soft.repo
yum install serverbackup-agent
Or…
# nano /etc/yum.repos.d/r1soft.repo
Add…
[r1soft]
name=R1soft Repository Server
baseurl=http://repo.r1soft.com/yum/stable/$basearch/
enabled=1
gpgcheck=0
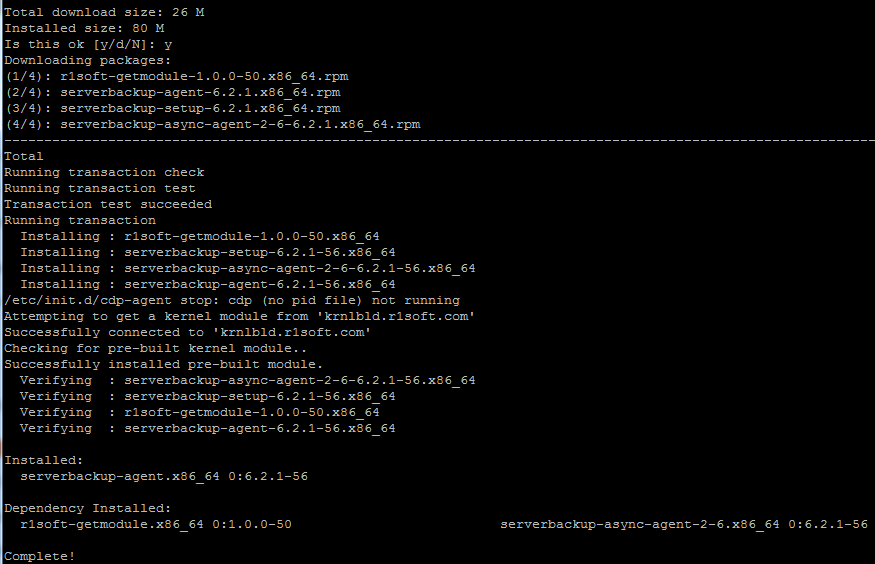
Save the files and then run ‘yum install serverbackup-agent’:
# yum install serverbackup-agent
Next, restart the agent:
# /etc/init.d/cdp-agent restart
/etc/init.d/cdp-agent restart: cdp not running, trying to start
/etc/init.d/cdp-agent restart: cdp started
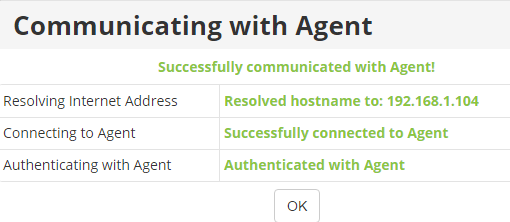
Next, we need to get the Server Backup Manager Server key from the Manager server:
NOTE: If the server manager is running on a different port than port 80, you will need to include the port in the URL. This server manager is on http port 26080. You can replace the port with port 80 if needed:
# serverbackup-setup --get-key http://192.168.1.103:26080
Key '192.168.1.103' successfully installed
If you get a connection errr - check your firewall:
# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Tue 2017-02-28 17:56:33 CST; 3 days ago
Docs: man:firewalld(1)
Main PID: 665 (firewalld)
CGroup: /system.slice/firewalld.service
└─665 /usr/bin/python -Es /usr/sbin/firewalld --nofork --nopid
Warning: Journal has been rotated since unit was started. Log output is incomplete or unavailable.
Add the port on the linux agent server to allow connection from the R1Soft server manager:
# firewall-cmd --permanent --zone=public --add-port=1167/tcp --permanent
success
Reload the firewall:
# firewall-cmd --reload
success
You can now safely add this target server to the Manager Server (See Installing R1Soft Linux Manager Server on CentOS)
**** If the agent is installed on CentOS 7, or if you have installed kernel-devel / kernel-headers and ‘r1soft-setup –get-module’ is still failing, check http://repo.r1soft.com/modules/ for the associated kernel and driver.
You can download the appropriate module to /lib/modules/r1soft/ run insmod $module to insert the module and /etc/init.d/cdp-agent restart to load hcpdriver.
Once CDP-agent is restarted, you can verify that the module is loaded via lsmod | grep hcp.
# cd /lib/modules/r1soft/
# wget http://repo.r1soft.com/modules/Centos_7_x64/hcpdriver-cki-3.10.0-693.11.6.el7.x86_64.ko
# insmod hcpdriver-cki-3.10.0-693.11.6.el7.x86_64.ko
# /etc/init.d/cdp-agent restart
# lsmod | grep hcp
# hcpdriver 81014 4