https://www.digicert.com/ssl-certificate-installation-microsoft-iis-8.htm
Category: Windows 2012 Server
Definition of profiles in Microsoft words:
Domain. Windows automatically identifies networks on which it can authenticate access to the domain controller for the domain to which the computer is joined in this category. No other networks can be placed in this category.
Public. Other than domain networks, all networks are initially categorized as public. Networks that represent direct connections to the Internet or are in public places, such as airports and coffee shops should be left public.
Private. A network will only be categorized as private if a user or application identifies the network as private. Only networks located behind a NAT device (preferably a hardware firewall) should be identified as private networks. Users will likely want to identify home or small business networks as private.
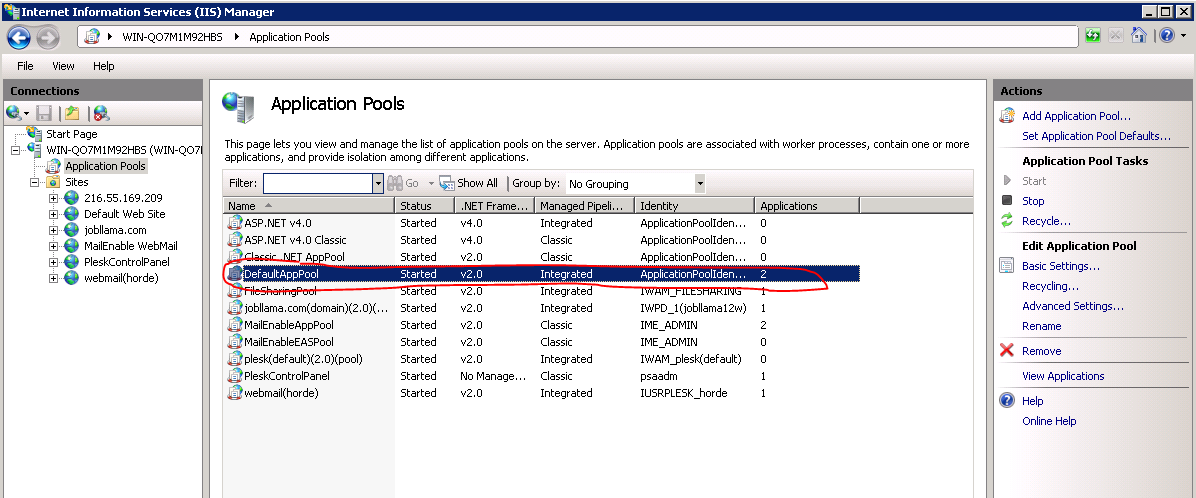
The solution for me was to change the .NET framework version in the Application Pools from v4.0 to v2.0 for the Default App Pool:
21
down vote
If, like me, you need to target v4 but can only build with .net 3.5, follow the instruction here. Just replace in your web.config the whole content of the
<configSections>
<sectionGroup name="system.web.extensions" type="System.Web.Configuration.SystemWebExtensionsSectionGroup, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35">
<sectionGroup name="scripting" type="System.Web.Configuration.ScriptingSectionGroup, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35">
<section name="scriptResourceHandler" type="System.Web.Configuration.ScriptingScriptResourceHandlerSection, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" requirePermission="false" allowDefinition="MachineToApplication"/>
<sectionGroup name="webServices" type="System.Web.Configuration.ScriptingWebServicesSectionGroup, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35">
<section name="jsonSerialization" type="System.Web.Configuration.ScriptingJsonSerializationSection, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" requirePermission="false" allowDefinition="Everywhere"/>
<section name="profileService" type="System.Web.Configuration.ScriptingProfileServiceSection, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" requirePermission="false" allowDefinition="MachineToApplication"/>
<section name="authenticationService" type="System.Web.Configuration.ScriptingAuthenticationServiceSection, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" requirePermission="false" allowDefinition="MachineToApplication"/>
<section name="roleService" type="System.Web.Configuration.ScriptingRoleServiceSection, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" requirePermission="false" allowDefinition="MachineToApplication"/>
</sectionGroup>
</sectionGroup>
</sectionGroup>
Connect to your server via Remote Desktop
Click simultaneously on the Windows logo + R to open the “Run” dialog and execute the “cmd” command
Open the registry editor by typing the “regedit” command
Search for this registry subkey:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\TerminalServer\WinStations\RDP-Tcp\PortNumber
Double-click or right-click on the “PortNumber” registry subkey, select the decimal base and type the port number of your choice (the default port is 3389, in this example, we selected port 3390). Click on “Ok” to save your selection.
IMPORTANT: Make sure that remote access to your server through the new port is authorized in your Windows firewall before executing the next step. Add a new Firewall Port Incoming rule allowing the port number.
Exit the registry editor
Restart your server
After the reboot, specify the Remote Desktop port number.
Resources:
http://www.techrepublic.com/blog/the-enterprise-cloud/changing-the-rdp-listening-port-on-windows-server/
http://www.sql-server-performance.com/2010/transactional-replication-2008-r2/
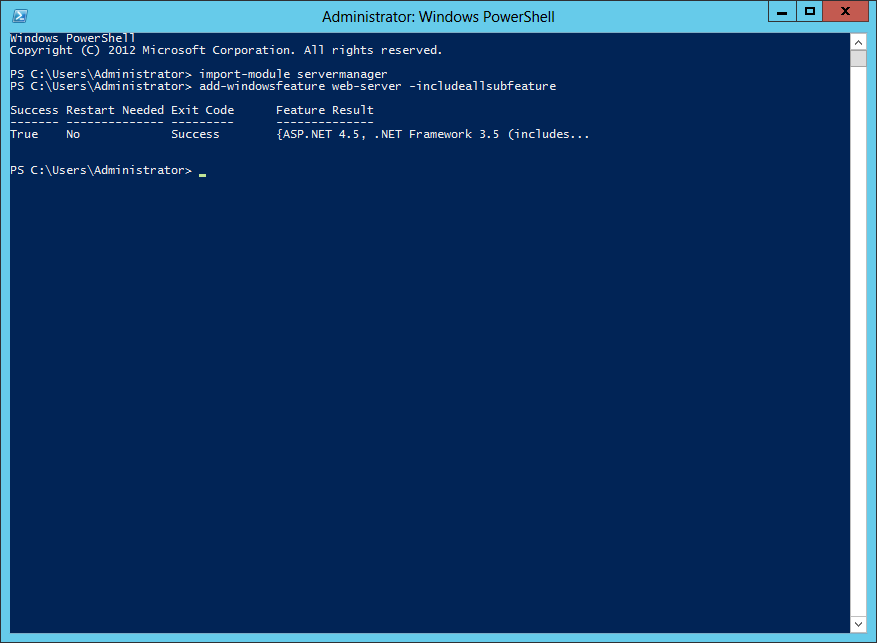
To install the role using PowerShell, use these steps. PowerShell must be run using Administrator rights. Installing IIS and all subfeatures can be run in 2 commands:
Import-module servermanager Add-windowsfeature web-server –includeallsubfeature
To install the role using Server Manager, follow these steps:
You should be able to check the Event Viewer and go through the Security section to see the Audit Successes and Failures for logins. If you are on the general tab, there is a box at the top (which you have to scroll through) that would say why it failed if it was a Failure and lower in that box it would say the source network address and the workstation name that was connecting.
Update:
To view the RDP logins:
Event Viewer > Applications and Services logs > Microsoft > Windows > TerminalServices-RemoteConnectionManager > Operational
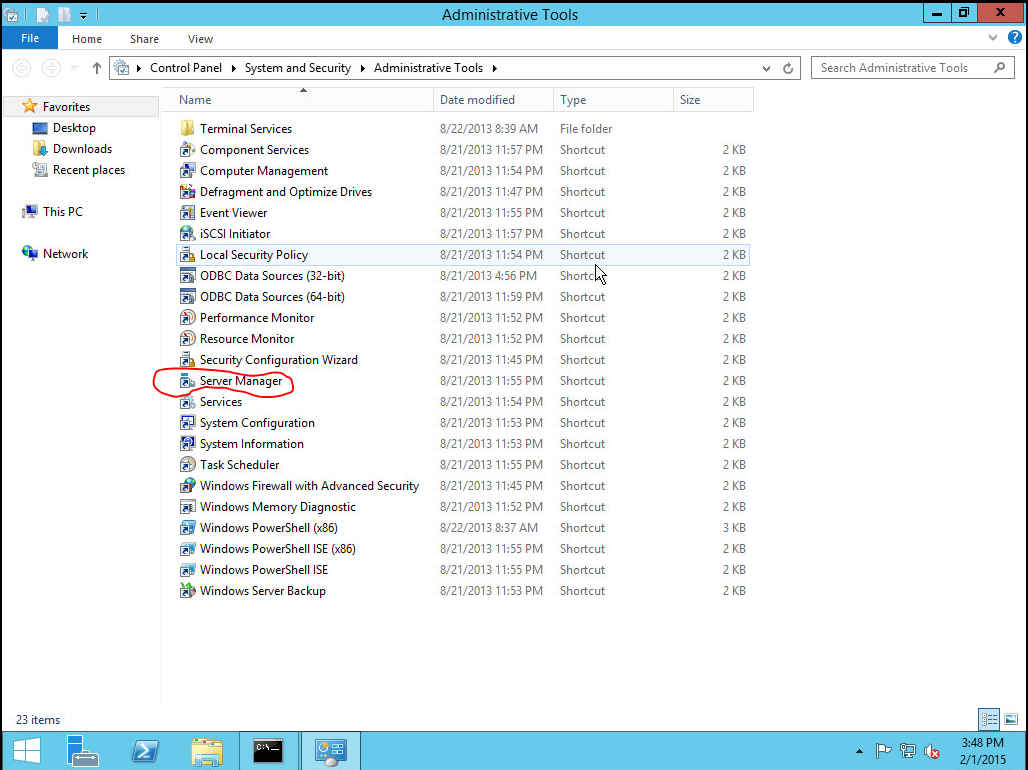
Open Server Manager. To open Server Manager, click Start, point to Administrative Tools, and then click Server Manager.